There’s no way to prevent a ransomware attack. Hackers will try to worm their way into your systems in the hopes of even the smallest treasure. The only thing you can do is stop them from getting the satisfaction.
In an age of prolific malware and constant cyber attacks, protection needs to start at the infrastructure level. If you approach your infrastructure strategically — adding air-gapped backups, building in separation — you can insulate your business from risk and create a platform for growth.
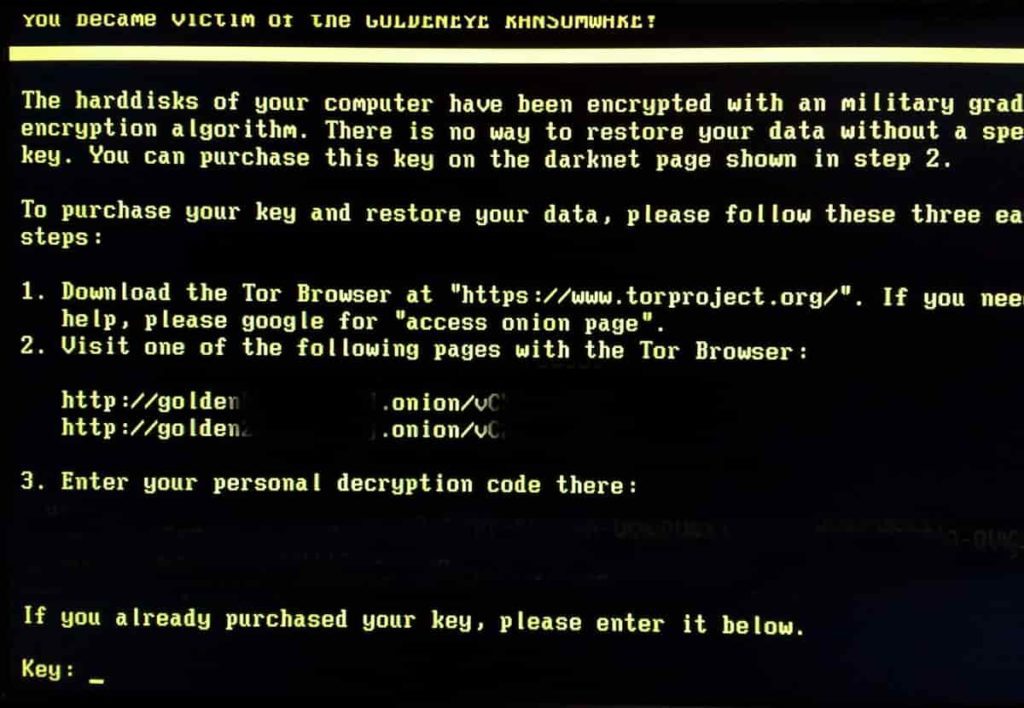
Ransomware exists to cripple your business so badly you’ll have no choice but to pay up to have your data and systems restored. It’s a nightmare scenario, but as long as you see it coming, it’s one you can avoid.
Understanding the basics: what is a ransomware attack?
By definition, a ransomware virus hijacks your data — taking it hostage in order to demand a ransom. It thrives on an attitude of “I’ll get to it.” All those backups you haven’t kept up-to-date or the systems you know need to be just a little more secure, that’s what it will exploit. All the tasks that piled up as chores to take care of during downtime become the reason your business is at a standstill.
Unlike some other types of malware, for ransomware to work, it has to map your entire infrastructure. That takes time — a single ransomware infection vector might burrow into your system for months, finding and controlling all of your backups before making itself known. After all, if you have a secure backup, all you have to do is restore from it and you’ve thwarted the hackers.
No, really. As long as your infrastructure is backed up properly, you’re most of the way to being able to recover from a ransomware attack. Again, your disaster recovery plan has to work.
Creating gaps for a ransomware attack vector to fall through
It’s not exactly as simple as making a copy and calling it a day. But backing up your applications and data to prevent ransomware isn’t too much more complicated. The key is making sure those backups are architected in a way that they can’t be accessed.
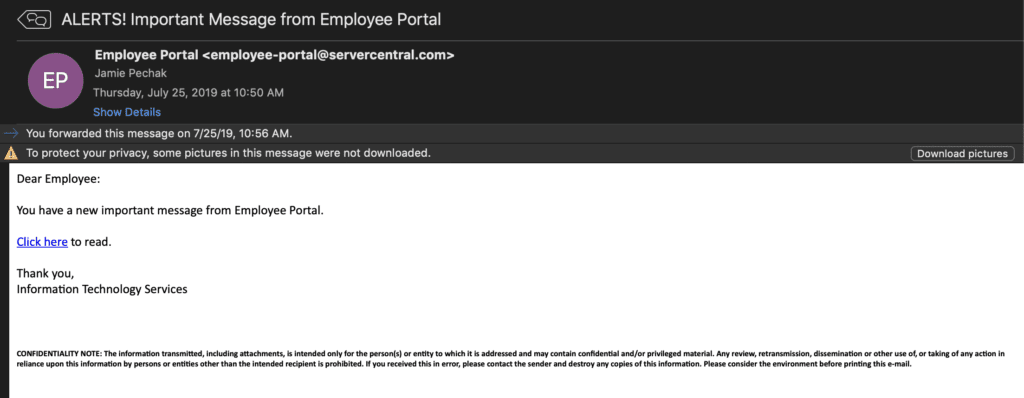
Think about this: An errant employee clicks the wrong email, opening up a door to a ransomware attack. Inside the system, the virus isn’t content with just the information that the employee can access. Instead, it waits and looks for opportunities to move deeper and deeper into the system, hopscotching across any connections it can find.
Most infrastructure is built like a web — everything is connected through something. If you want to prevent ransomware infections from spreading, all you have to do is clip a few of those strings, breaking the connections that allow the virus to penetrate every part of your system.
There are lots of ways to do this. Air-gapped backups build in literal distance between your backups and your main system, while off-site backups keep a copy of everything securely locked away. If you’re diligent about keeping those backups up-to-date, getting rid of ransomware is simply a matter of cutting off the infected parts of your infrastructure and restoring your backups.
An example of ransomware protection done right
Take a services company that we work with at Deft. The firm suffered a ransomware attack at the start of 2019. For several months, hackers were sitting in its systems, looking for a way to move around the various servers and searching for where backups were kept.
They didn’t find it. The company uses Deft’s managed backup service, so we had long ago built a system that automatically captures and stores regular backups separately from the production environment where everyone works. Try as they might, hackers never could get to the backups.
When they finally gave up and activated the ransomware encryption, we flipped the proverbial switch to move the backups to a new isolated production environment and create a new, “clean” version of the production systems. Like its predecessor, this one was similarly air-gapped away from the day-to-day infrastructure. The hackers got nothing, and the customer had no interruption to its normal operations.
How to prevent ransomware? Pretend it’s inevitable
That’s because it is inevitable. If you focus only on ransomware prevention strategies, you’ll fail. Eventually, someone is going to click the wrong thing, join the wrong network, leave their connected device in the wrong place. There’s just no way to avoid malware altogether.
Instead, we prepare for it. At Deft, we watch the strategies of hackers full-time, reverse engineering their techniques and finding ways to interrupt them. We may not be able to keep the world safe from malware attacks, but we can keep them from disrupting your business. We have the processes, tools and — most importantly — 24/7/365 experts in place to follow the best practices for avoiding malware.
There’s no doubt that your IT team is working hard to keep your data and systems secure. But backups to protect against future attacks are the definition of work that’s critical, but not urgent. Realistically, it gets punted for more pressing concerns, never getting the time and resources needed to do it properly until it’s too late.
If you want to make sure you’re secure — and free IT up to do better things — let’s talk through the disaster recovery options and see which one might work for you.
