If you’re reading this article on how to protect against DDoS attacks before you get hit with one, congratulations. DDoS attacks happen tens of thousands of times per day:
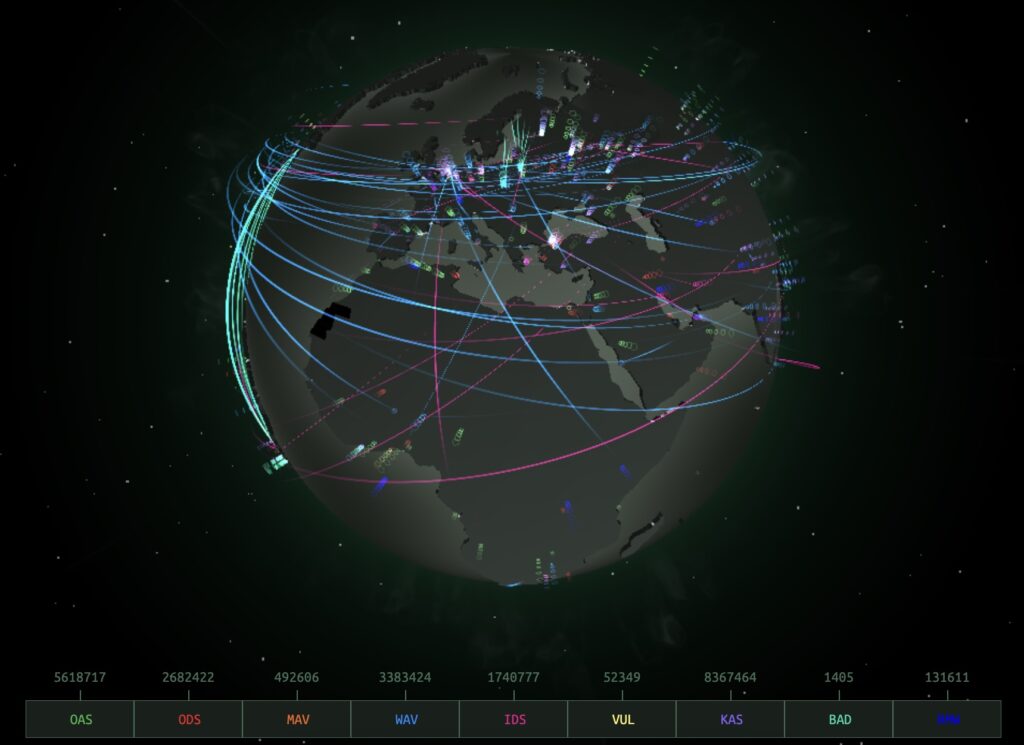
If you’re in the thick of fending off illegitimate traffic, you’re in the right place.
On a long enough timeline, a denial of service attack is inevitable for any business. So let’s start at the beginning.
What’s a DDoS attack?
A distributed denial of service (DDoS) attack is a type of cyber attack that involves flooding a website or server with so much traffic that it becomes unavailable to legitimate users. The easiest way to do that is to use bots — a zombie army of devices infected with malware.
Users download malware by mistake by clicking on a phishing scam link or file:
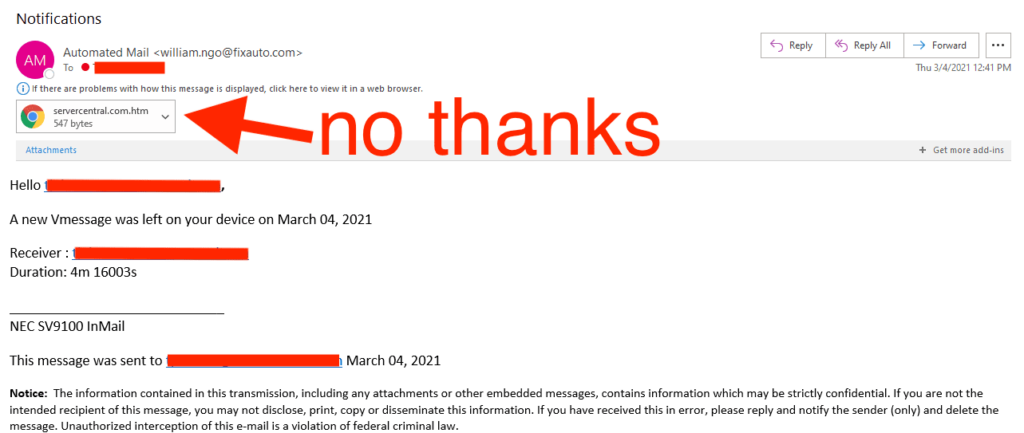
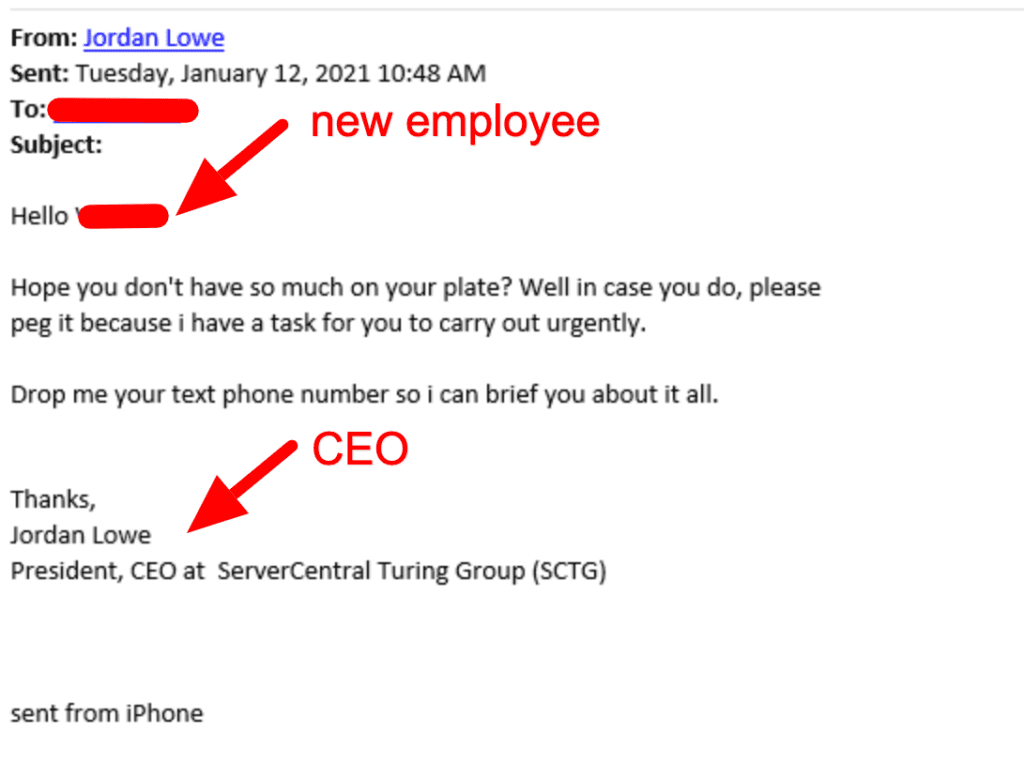
The malware then turns the device into a remotely controlled zombie. The user is no longer in control of the device. Instead, the master of the botnet controls it. When the time comes, the master of the botnet sends a request to the device and it joins the attack. They start sending thousands of connection requests to the target. Networks and servers have limited capacity, so they slow down or crash entirely.
Whatever’s on that server goes down — like the company’s website and databases — until the attack stops. Most companies can recover from the damage, but it’s still massively inconvenient and potentially dangerous for things that rely on a constant connection to servers, like medical systems.
When Anonymous targeted Boston Children’s Hospital, the damage was palpable:
- Inability to send electronic prescriptions to pharmacies
- Email downtime for departments where email supports critical processes
- Inability to access remotely hosted electronic health records (EHRs)
What you can do about it
You need to work with a provider who handles DDoS attacks all day, every day — preferably one with a fully-staffed Network Operations Center (NOC). We block the bad traffic when it comes in.
A service like DDoS protection proactively monitors network traffic, including the traffic to a website or a specific server. When traffic has an abnormal spike, DDoS mitigation kicks in, letting your customer traffic in and blocking anything malicious.
How likely are my servers to be attacked?
If devices are connected to the internet, the likelihood of your business’s servers being hit by a DDoS attack at some point is 100%. there is the possibility of a DDoS attack.
Once everyone in your organization really understands that this is an inevitability, not a possibility, you can start to have the necessary conversations. Planning for an attack at some point is just good business — whether you choose to pay for protection upfront or create a fund for emergency DDoS mitigation.
How to protect against DDoS attacks in 3 steps
As easy as it is to start a DDoS attack — from anywhere, at any time — you really won’t know until it hits you. Any plan must account for this. Your plan should be well-defined, clear, and ready to put into practice at a moment’s notice, preferably automatically. Everyone needs to be on the same page regarding what is going to happen because it all has to happen fast.
Here are the basic steps you’ll need answers for:
1. Monitoring traffic to your servers
To know what a giant spike in traffic looks like for your business, you need a baseline for what is normal. At Deft, we monitor the traffic patterns for all of our clients who are connected to our network and help them define parameters for what unusual looks like.
We also have formal protocols in place ahead of time for what happens when we do detect suspicious traffic. Some businesses err on the side of caution, and want to put DDoS mitigation in place the second something looks off. Others want to be notified, so they can assess the situation in real time and determine the best course of action. We work with our clients as true partners to find their risk tolerance and then put in place the necessary protocols to meet it.
2. Separating legitimate traffic — and stopping a DDoS attack
Sophisticated DDoS scrubbing software basically acts as a virtual bouncer, with your servers being the highly sought-after nightclub. It looks at everyone trying to come in the door and decides who should get in, and who’s getting kicked out.
Everyone who uses Deft as their connectivity partner has access to our Advanced DDoS scrubbing systems. Whether they choose to prepare protection ahead of time or put it into place during an attack, there’s always an option that’s better than shutting down the server and hoping all that good traffic doesn’t mind being thrown out with the bad.
DDoS mitigation can take that spike in traffic and keep your operations running, even if they may be running a little slower, until the attack stops. The users you want can still access your service, minimizing upset customers and loss of profit.
3. Building a network infrastructure that can withstand an attack
Since a DDoS attack is inevitable, it’s best to build network infrastructure with that in mind. At Deft, we work with clients to prepare for spikes in traffic all the time, whether it comes from the holiday season, a TV appearance, or a DDoS attack.
A few best practices can go a long way, even covering the effects of a smaller DDoS attack completely:
- Rate Limiting: Certain types of network traffic are required but are normally low in volume. Some of these are also common attack vectors for DDoS. You can rate limit these types of traffic to help protect your network. For example, 1 Mbps of DNS traffic may be normal. 100 Mbps may be a normal spike while 1 Gbps or more most likely identifies attack traffic — unless you’re a DNS provider. This puts a cap on how many times a certain action can be taken by a single IP address trying to access a site. A human is only going to hit refresh on a page so many times, and so fast. A bot, on the other hand, can flood an unprotected system with repetitive actions, taking it down with very little work.
- Content Delivery Network (CDN): A CDN uses proxy networks to distribute your site’s content from the servers closest to your user’s geographical location. It also comes in handy to shift traffic to different servers during a DDoS attack.
- Load Balancers: These ensure that no one server is overworked by traffic. When more traffic than normal hits your site, the traffic is distributed across numerous servers.
- Web Application Firewall (WAF): This protects your web applications from application layer attacks. It keeps the applications from being the open door to your business and your customers’ sensitive data.
Finding the right partner for DDoS protection
When looking for the right partner to provide DDoS mitigation services, there are a lot of questions to ask. One you don’t need to worry about is “Will it happen to me?” The answer is a resounding yes.
Instead, focus your efforts on finding an infrastructure partner who’s ready for that reality. You want a team with systems in place to minimize damage and enough communication to keep anxiety in check during an attack.
Above all, know that protecting against a DDoS attack is not a one-time fix. It’s not enough to have a plan — it must be communicated well and updated as risks evolve.
